Room URL: TryHackMe | XSS
Explore in-depth the different types of XSS and their root causes.
Task 1: Introduction
Cross-site scripting (XSS) remains one of the common vulnerabilities that threaten web applications to this day. XSS attacks rely on injecting a malicious script in a benign website to run on a user’s browser. In other words, XSS attacks exploit the user’s trust in the vulnerable web application, hence the damage.
Room Prerequisites
Below is a list of the rooms that you can use to fill any knowledge gaps before starting with this room:
Optional: Python Basics
Learning Objectives
Upon the completion of this room, the user should gain a more in-depth understanding of XSS, in particular:
Reflected XSS
Stored XSS
DOM-based XSS
How to protect against XSS
Task 2: Terminology and Types
This task is about:
XSS Overview:
XSS is a vulnerability allowing attackers to inject malicious scripts into web pages viewed by other users.
It bypasses the Same-Origin Policy (SOP), a security mechanism in modern web browsers preventing scripts from one page accessing data on another.
JavaScript in XSS:
Understanding JavaScript is crucial for comprehending and executing XSS exploits.
Different browsers may process code snippets differently, necessitating adaptation of exploits to the target browser.
Tools like the browser console facilitate experimentation with JavaScript functions.

Types of XSS:
Reflected XSS: Relies on user-controlled input reflected back to the user, such as search queries. Attackers embed malicious scripts in input fields to execute on other users' browsers.
Stored XSS: Exploits user input stored in the website's database, like product reviews. Malicious scripts inserted by attackers execute when other users view the stored content.
DOM-based XSS: Exploits vulnerabilities within the Document Object Model (DOM) to manipulate page elements without server interaction. It's less common than reflected and stored XSS.
Which XSS vulnerability relies on saving the malicious script?
Answer: Stored XSS
Which prevalent XSS vulnerability executes within the browser session without being saved?
Answer: Reflected XSS
What does DOM stand for?
Answer: Document Object Model
Task 3: Causes and Implications
Cross-site scripting (XSS) is a web security vulnerability that allows an attacker to inject malicious scripts into a web page viewed by other users. As a result, the unsuspecting users end up running the unauthorized script in their browsers, although the website they are visiting is trusted to be benign. Therefore, XSS can be a severe threat because it exploits users’ trust in a site.
What Makes XSS Possible
XSS vulnerabilities happen in web apps because of a few common reasons:
Unfiltered User Input: Imagine a form with a blank space for your name. If the website doesn't check what you type, attackers could enter malicious code disguised as a name. This code could then steal your information or harm the website.
Encoding Errors: Websites need to translate certain characters for proper display. If this process isn't done correctly, attackers can manipulate those characters to inject their own harmful scripts.
Security Misconfiguration: Think of security settings like locks on a door. If they're not set up right, even a locked door might not keep attackers out. For example, a setting allowing any script to run is like having a lock that opens with any key.
Outdated Tools: Imagine building a house with weak materials. Just like old building tools might not create secure structures, outdated website development tools might lack proper safeguards against attacks.
Vulnerable Third-Party Add-ons: Websites often use pre-built components to save time. If these components have weaknesses, they can be exploited by attackers to gain access to the main website, even if the website itself is secure.
Implications of XSS
Here's what attackers can do with XSS:
Session hijacking: Attackers can use XSS to steal session cookies, allowing them to take control of a user's session and impersonate them.
Phishing and credential theft: By exploiting XSS, attackers can present fake login prompts to users, tricking them into revealing their credentials. For example, they might display a dialogue box asking users to log in to their cryptocurrency wallet.
Social engineering: Using XSS, attackers can create convincing pop-ups or alerts on trusted websites, leading users to click on malicious links or visit harmful websites.
Content manipulation and defacement: Attackers can use XSS to change website content, damaging the reputation of the company or organization that owns the website.
Data exfiltration: XSS enables attackers to access and steal any information displayed on a user's browser, including personal and financial data.
Malware installation: Sophisticated attackers can use XSS to distribute malware, such as drive-by download attacks, through vulnerable websites.
Based on the leading causes of XSS vulnerabilities, what operations should be performed on the user input?
Answer: validation and sanitization
To prevent XSS vulnerabilities, what operations should be performed on the data before it is output to the user?
Answer: Encoding
Task 4: Reflected XSS
I will jump into Question section TryHackMe explanation in this section is very easy.
Which one of the following characters do you expect to be encoded? ., ,, ;, &, or #?
Answer: &
Which one of the following characters do you expect to be encoded? +, -, *, <, =, or ^?
Answer: <
Which function can we use in JavaScript to replace (unsafe) special characters with HTML entities?
Answer: escapeHtml()
Which function did we use in PHP to replace HTML special characters?
Answer: htmlspecialchars()
Task 5: Vulnerable Web Application 1
The exploit code is ?k304=y%0D%0A%0D%0A%3Cimg+src%3Dcopyparty+onerror%3Dalert(1)%3E which is the URL encoding of: ?k304=y <img src=copyparty onerror=alert(1)>
The attached VM has the vulnerable server running at port 3923. You can reach the vulnerable server at http://10.10.167.254:3923 via your AttackBox’s browser.
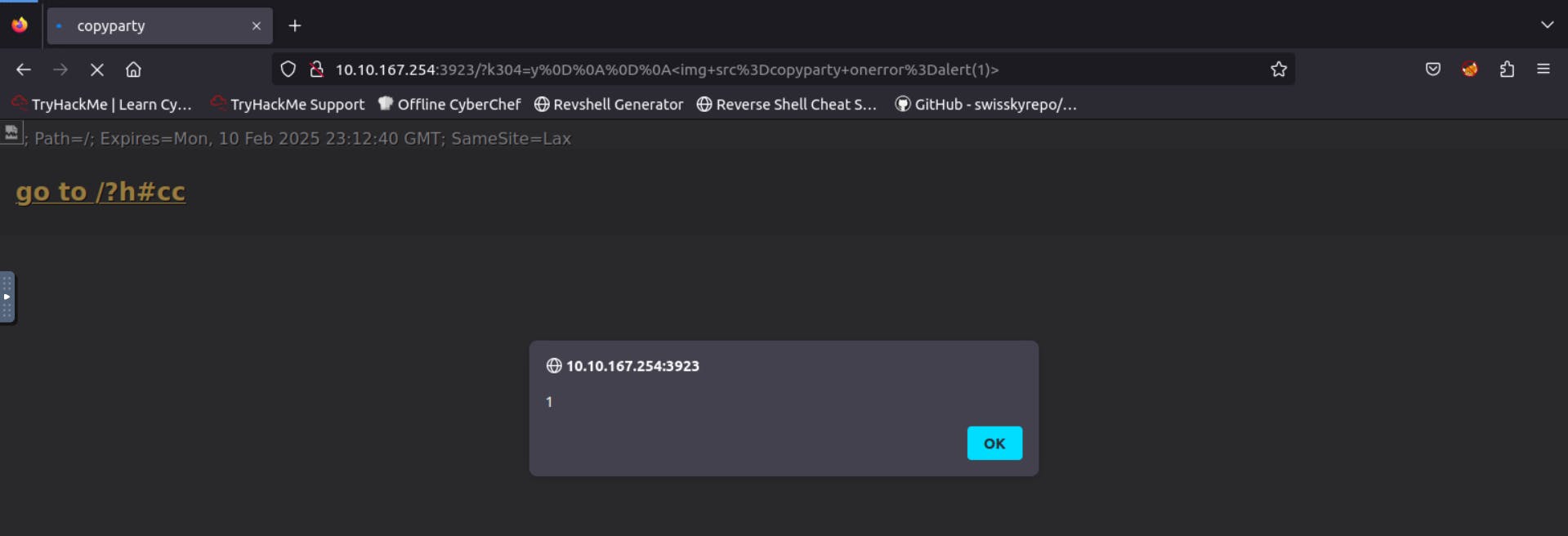
What type of vulnerability is it?
Answer: Reflected XSS
Use the above exploit against the attached VM. What do you see on the second line after go to?
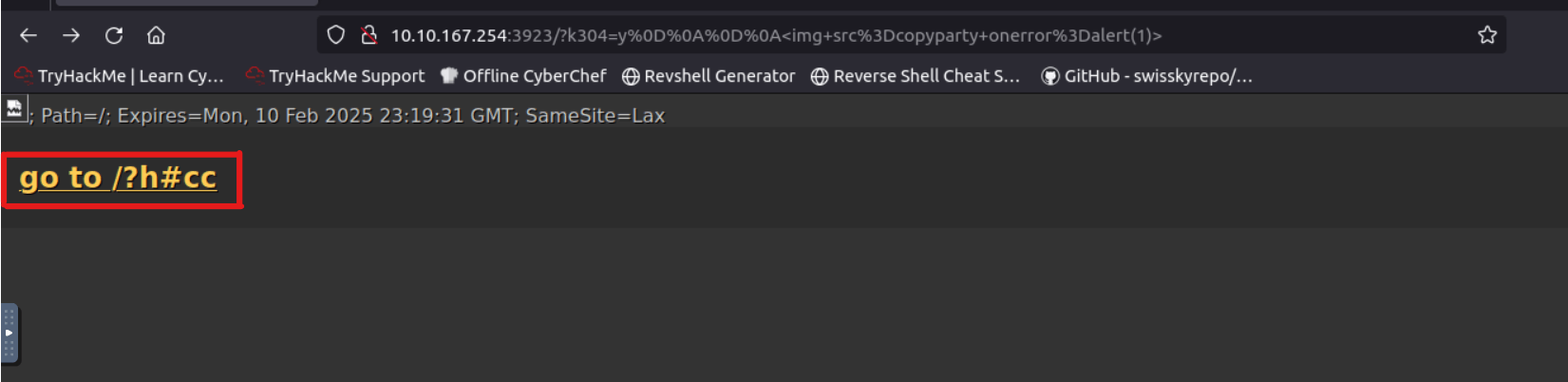

Answer: /?h#cc
Task 6: Stored XSS
What is the name of the JavaScript function we used to sanitize the user input before saving it?
Answer: sanitizeHTML()
Which method did we call in ASP.Net C# to sanitize user input?
Answer: HttpUtility.HtmlEncode()
Task 7: Vulnerable Web Application 2
What type of vulnerability is it?
Answer: Stored XSS
Go to the contact page and submit the following message <script>alert(document.cookie)</script>. Next, log in as the Receptionist. What is the name of the key from the third displayed key-value pair?
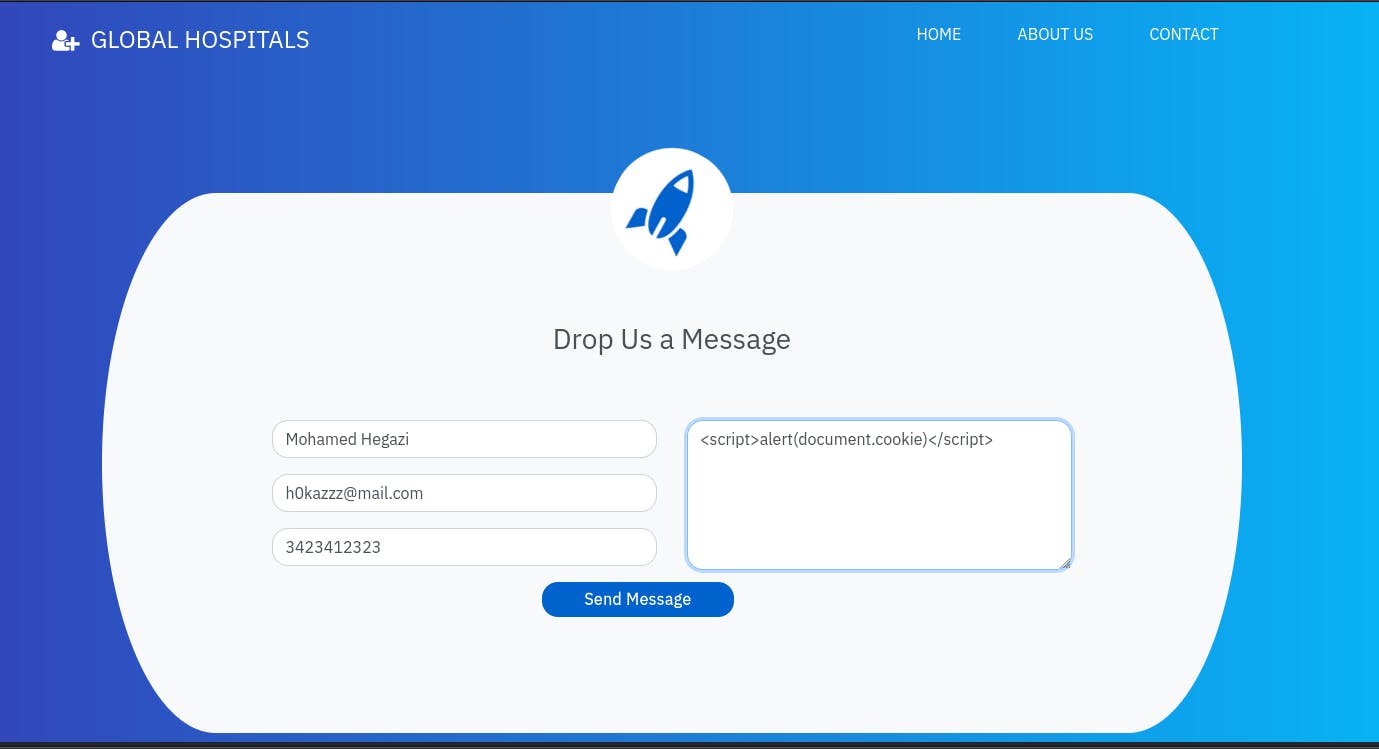
Navigate to home page and login as the Receptionist.
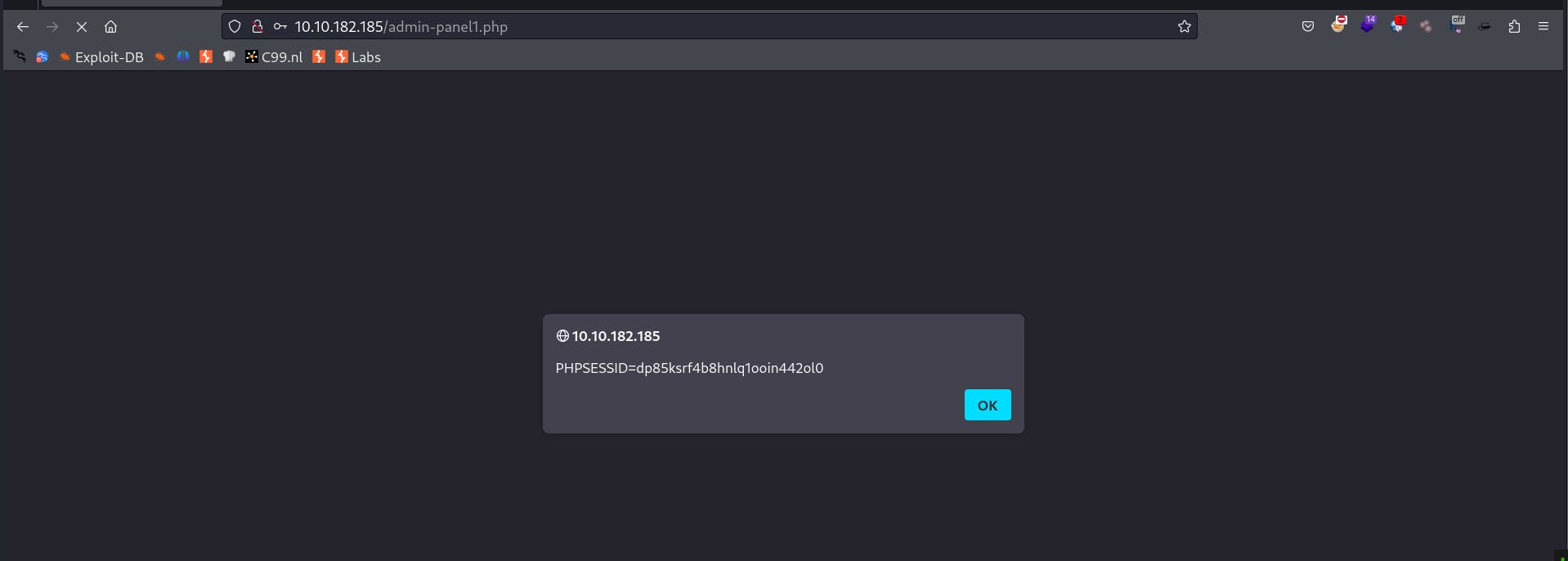
Answer: PHPSESSID
Task 8: DOM-Based XSS
DOM-based XSS is reflected via the server. (Yea/Nay)
Answer: Nay
DOM-based XSS happens only on the client side. (Yea/Nay)
Answer: Yea
Which JavaScript method was used to escape the user input?
Answer: encodeURIComponent()
Task 9: Context and Evasion
Which character does 	 represent?
Answer: TAB
Task 10: Conclusion
This room used a fictional static site to demonstrate one of the XSS vulnerabilities. Which XSS type was that?
Answer: Dom-based XSS

